This next challenge is about the number patterns.. You might have heard about Fibonacci series, multiplicadditive sequence, Digit Product Sequences and many more, where you have to take the number and add/multiply/divide/subtract some number to get another number, and perform the same actions of that number to get another number and so on.. So, as we can see from the title of this challenge (That is "Follow the pattern" by the way), we understand that it has to do something with number sequences or pattern. So lets solve it..
Site: CanYouHackIt (http://canyouhack.it/)
Challenge: Logic > Logic Challenge 4 > Follow the pattern
You might think that this doesn't make any sense or what does this have to do with hacking or whatever.. Remember a few points here.. This is basic reasoning. This can be used in cryptoanalysis.. Cryptography works with the base of mathematics.. If you understand basic reasoning, you can understand cryptography easily.. Or at least that's what logically can be fit here..
So lets analyse the sequence, shall we ?
The sequence is 2, 3, 5, 11, 19, 41. 73, 139, ??? .. We need to find the number which comes after 139 to get our password..
Analysis:
1. This is not simply the sequence of prime number because if it was, it should have stated 7 and 13 in mid way.. But it didn't. which means, this is not the prime number sequence..
2. This is not Fibonacci series either, because if it was, there would have been 8 after 5 in the sequence..
3. Now we can think of adding previous two number and try to get next number, this method fails at 4th number -> 2+3+5 = 10 but the number is 11..
4. We can think of subtract previous two numbers and multiply with some randomly suitable number to get the next number, but you will soon realize that this method isn't working either in later stages..
So here is the solution..
See below image of prime numbers:
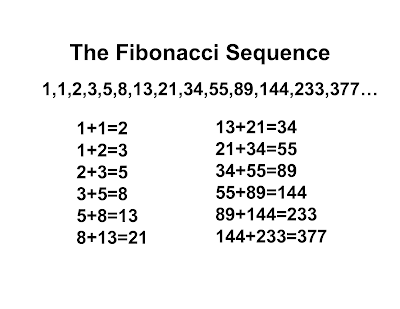
See below image of Fibonacci series:
Now let's start:
Fibonacci series' first number is 1
Take 1st prime number -- That's 2
Fibonacci series' second number is 1
We already took 1st prime number - Ignore
Fibonacci series' third number is 2
Take 2nd prime number -- That's 3
Fibonacci series' fourth number is 3
Take 3rd prime number -- That's 5
Fibonacci series' fifth number is 5
Take 5th prime number -- That's 11
Fibonacci series' sixth number is 8
Take 8th prime number -- That's 19
Fibonacci series' seventh number is 13
Take 13th prime number -- That's 41
Fibonacci series' eighth number is 21
Take 21st prime number -- That's 73
Fibonacci series' ninth number is 34
Take 34th prime number -- That's 139
Fibonacci series' tenth number is 55
Take 55th prime number -- That's 257, We got our number.. That's the password for this challenge..